The Hacker's New Co-Pilot: AI
Imagine a dogfight between two fighter pilots. One is a seasoned ace, a defender with years of experience who knows their aircraft inside and out. The other is a moderately skilled attacker. In a fair fight, the ace has the advantage.
Now, imagine the attacker's plane is suddenly upgraded with an AI co-pilot. This AI can calculate the perfect firing solution in a microsecond, predict the defender's every move, and manage the aircraft's systems with flawless efficiency. The human attacker is no longer just a pilot; they are the mission commander for a machine that thinks at the speed of light.
The defender's skill hasn't changed, but the battlefield has become impossibly asymmetric. They are no longer fighting just a pilot; they are fighting a pilot and a machine.
This is the new reality of cybersecurity. For years, we've been the ace defenders, relying on our experience and tools. But today, our adversaries have an AI co-pilot, and it's accelerating their attacks beyond human scale.
The Force Multiplier: How AI Is Industrializing Attacks
Artificial intelligence isn't just another tool for attackers; it's a force multiplier that fundamentally changes the economics of cybercrime. It makes sophisticated attacks cheap, fast, and easy to scale, creating a new, dangerous imbalance.
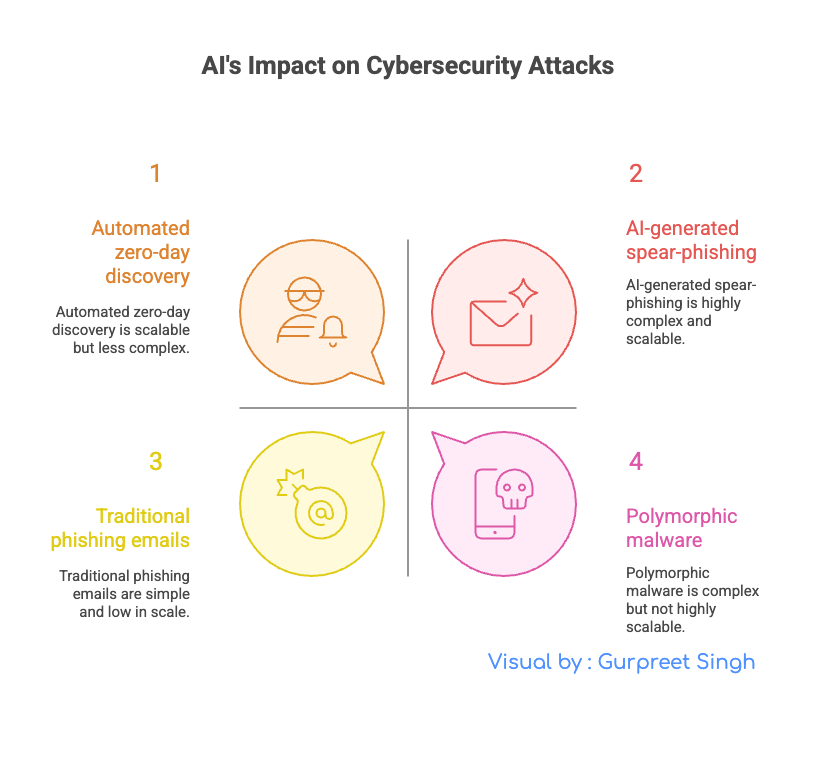
Hyper-Personalized Deception at Scale: Generic phishing emails with bad grammar are a thing of the past. Generative AI can now craft millions of unique, context-aware spear-phishing emails in perfect, native-level language. It can scrape LinkedIn to reference a target's real colleagues and projects. We're also seeing the rise of AI-generated voice clones, where an attacker can fake a CEO's voice in a "vishing" (voice phishing) call with terrifying accuracy.
Automated Discovery of Zero-Day Flaws: Previously, finding a "zero-day" vulnerability—a flaw no one else knows about—required immense skill and time. Now, attackers can use AI to analyze code and software at a massive scale, hunting for novel weaknesses far faster than any human security research team.
Malware That Thinks for Itself: AI is enabling the creation of polymorphic and metamorphic malware. This is malicious code that can actively change its own structure and behavior to evade detection. It's like fighting an enemy that wears a new disguise every second. Traditional signature-based defenses, which look for a known "face" of malware, are becoming increasingly useless against an enemy with a million faces.
This AI-driven assault creates a deafening "signal-to-noise" problem. When attackers can launch thousands of sophisticated, automated attacks at once, human security teams are quickly overwhelmed, unable to distinguish the critical threat from the background noise.
The Strategic Pivot: Adapting Your Defense for the AI Era
You cannot win a dogfight against an AI with yesterday's tactics. To restore balance, defenders must embrace a new playbook that leverages our own AI and elevates the role of our human experts.
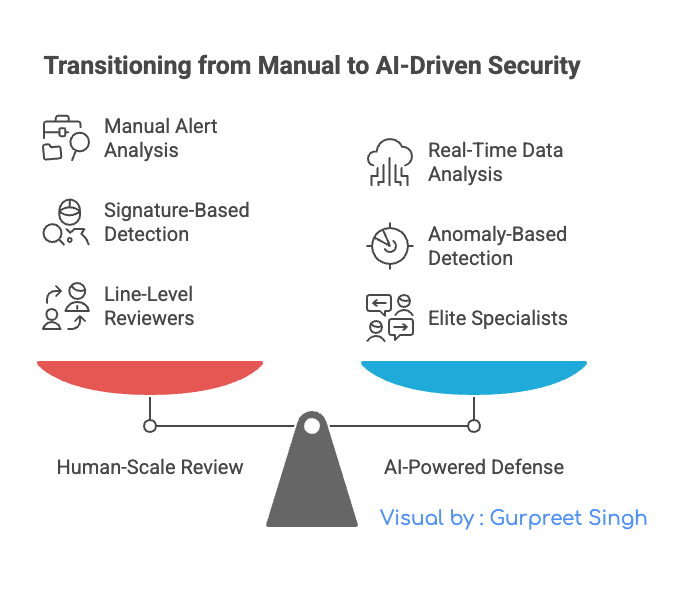
Pivot #1: From Human-Scale Review to AI-Powered Defense
The Old Playbook: Human analysts sit in a Security Operations Center (SOC), manually reviewing streams of alerts from firewalls and antivirus tools. It's a heroic but unsustainable effort, like trying to catch raindrops in a hurricane.
The New Playbook: You fight AI with AI. Deploy defensive AI platforms that can analyze trillions of data points in real-time. These systems learn the unique "rhythm" of your organization—a baseline of normal behavior. They don't need a signature to know something is wrong; they can spot the subtle anomaly of an AI-driven attack instantly. This allows your human experts to focus only on the handful of truly critical, verified threats that the AI surfaces, acting as elite specialists rather than line-level reviewers.
Pivot #2: From Reactive Patching to Proactive Exposure Management
The Old Playbook: A new vulnerability is announced. A frantic scramble begins to find all affected systems and deploy a patch, racing against attackers who are already exploiting it.
The New Playbook: Use AI-driven tools to continuously map your entire attack surface, both inside and out. An AI-powered exposure management platform can think like an attacker, proactively identifying the most likely paths they would take to reach your "crown jewels." It answers the question not just "Are we vulnerable?" but "How would an attacker leverage this vulnerability to cause real damage?" This allows you to prioritize and fix the risks that truly matter before they are weaponized.
Pivot #3: From Security Awareness to Human Resilience
The Old Playbook: Train employees to spot the technical signs of a phishing email—a suspicious link, a generic greeting. This is a fragile defense against AI that can perfectly mimic legitimate communication.
The New Playbook: Elevate your people to be the final, critical line of defense against AI-generated deception. The training must shift from technical rules to critical thinking and context. An AI can fake the CFO's voice asking for an urgent wire transfer, but the human employee can ask the one question the AI can't answer: "This request is outside our normal process. Why?" You empower your people to be the human sensors who validate requests against business logic and common sense—a skill that remains uniquely human.
The rise of AI-enhanced threats is not a reason for despair. It is a catalyst for our own evolution. By embracing defensive AI to manage machine-speed threats and empowering our people to do what they do best—think critically—we can turn the new asymmetry back in our favor.