Your SOC Doesn't Need More Alerts; It Needs Fewer Decisions
This document argues that Security Operations Centers (SOCs) are often overwhelmed by a high volume of alerts, leading to alert fatigue and missed critical incidents. The key to improving SOC effectiveness is not necessarily generating more alerts, but rather focusing on reducing the number of decisions analysts need to make by improving alert fidelity, automating responses, and prioritizing high-risk events. This shift in focus allows analysts to concentrate on complex investigations and proactive threat hunting, ultimately strengthening the organization's security posture.
The Alert Avalanche
SOCs are drowning in alerts. Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), Endpoint Detection and Response (EDR) tools, and a myriad of other security solutions generate a constant stream of notifications, many of which are false positives or low-priority events. This "alert avalanche" has several detrimental effects:
Alert Fatigue: Analysts become desensitized to the constant barrage of alerts, leading to burnout and a higher likelihood of missing genuine threats.
Reduced Efficiency: Time is wasted investigating false positives, diverting resources from more critical tasks.
Delayed Response: The sheer volume of alerts can overwhelm analysts, delaying the response to actual security incidents.
Increased Risk: Critical incidents can be missed entirely, leaving the organization vulnerable to attack.
The problem isn't necessarily a lack of alerts; it's a lack of actionable alerts. SOCs need to move beyond simply collecting data and generating notifications to providing analysts with the context and information they need to make informed decisions quickly.
The Decision Deficit
The core issue is that SOC analysts are forced to make too many decisions. For each alert, they must determine:
Is this a genuine threat?
What is the potential impact?
What actions should be taken?
This decision-making process is time-consuming and error-prone, especially when analysts are under pressure and facing a high volume of alerts. The goal should be to reduce the number of decisions analysts need to make by automating as much of the process as possible and providing them with the information they need to make informed decisions quickly.
Strategies for Reducing Decisions
Here are several strategies for reducing the number of decisions SOC analysts need to make:
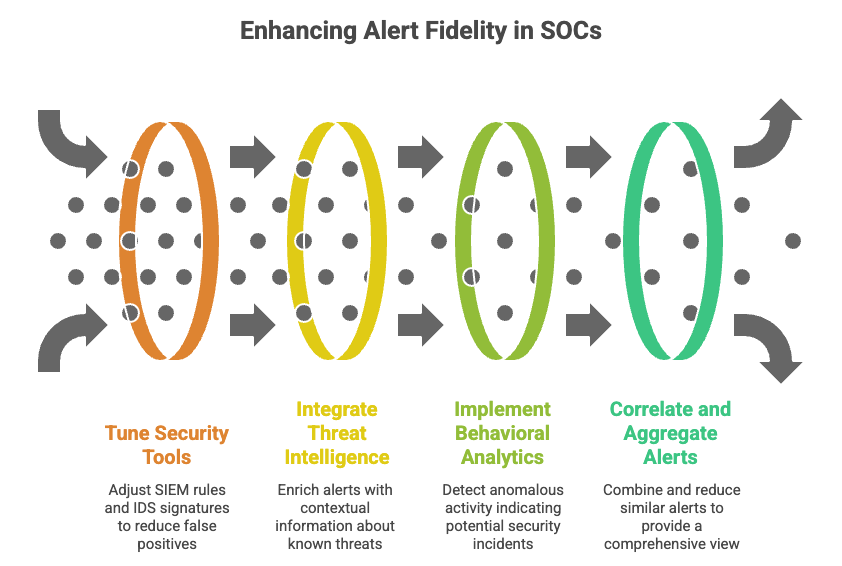
1. Improve Alert Fidelity
The first step is to improve the quality of alerts. This involves:
Tuning Security Tools: Fine-tune SIEM rules, IDS signatures, and other security tools to reduce false positives. This requires a deep understanding of the organization's environment and threat landscape.
Threat Intelligence Integration: Integrate threat intelligence feeds to enrich alerts with contextual information about known threats. This helps analysts quickly identify and prioritize high-risk events.
Behavioral Analytics: Implement behavioral analytics to detect anomalous activity that may indicate a security incident. This can help identify threats that might be missed by traditional signature-based detection methods.
Correlation and Aggregation: Correlate alerts from multiple sources to provide a more complete picture of the security incident. Aggregate similar alerts to reduce the overall volume.
By improving alert fidelity, SOCs can reduce the number of false positives and low-priority events that analysts need to investigate, freeing up their time to focus on more critical tasks.
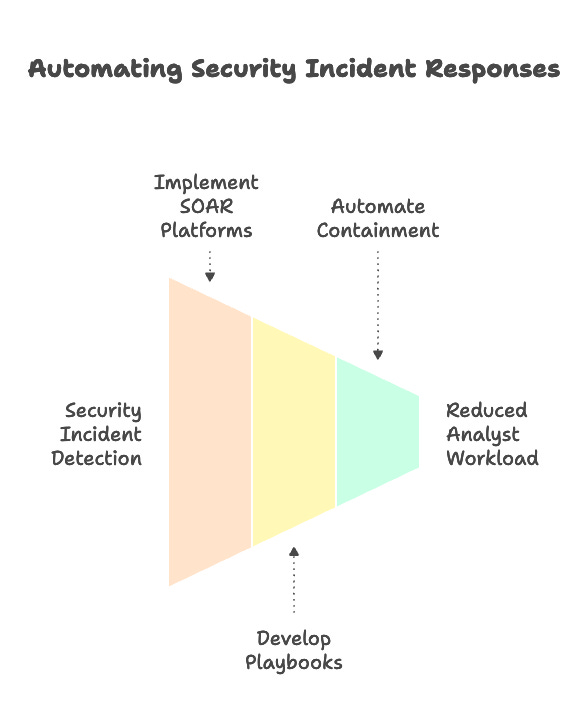
2. Automate Responses
Many security incidents can be handled automatically without human intervention. This can be achieved through:
Security Orchestration, Automation, and Response (SOAR): Implement SOAR platforms to automate repetitive tasks such as incident enrichment, containment, and remediation.
Playbooks: Develop playbooks that define the steps to be taken in response to specific types of security incidents. These playbooks can be automated using SOAR platforms.
Automated Containment: Implement automated containment measures such as isolating infected endpoints or blocking malicious IP addresses.
By automating responses, SOCs can significantly reduce the workload on analysts and improve their response time to security incidents.
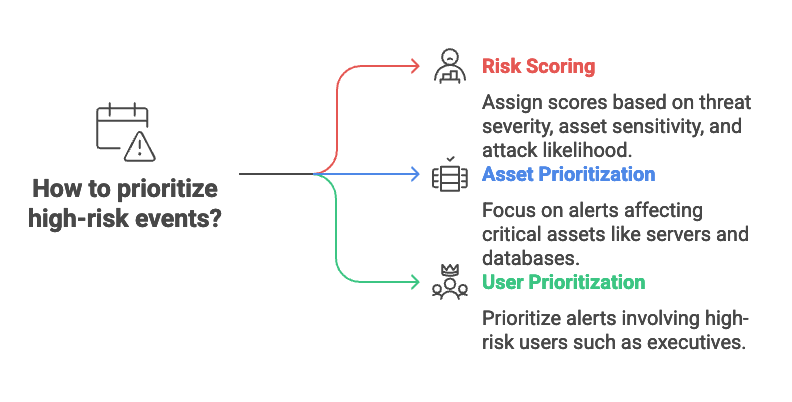
3. Prioritize High-Risk Events
Not all alerts are created equal. SOCs need to prioritize high-risk events that pose the greatest threat to the organization. This can be achieved through:
Risk Scoring: Assign risk scores to alerts based on factors such as the severity of the threat, the sensitivity of the affected assets, and the likelihood of a successful attack.
Asset Prioritization: Prioritize alerts affecting critical assets such as servers, databases, and network devices.
User Prioritization: Prioritize alerts involving high-risk users such as executives or system administrators.
By prioritizing high-risk events, SOCs can ensure that analysts focus their attention on the most important threats.
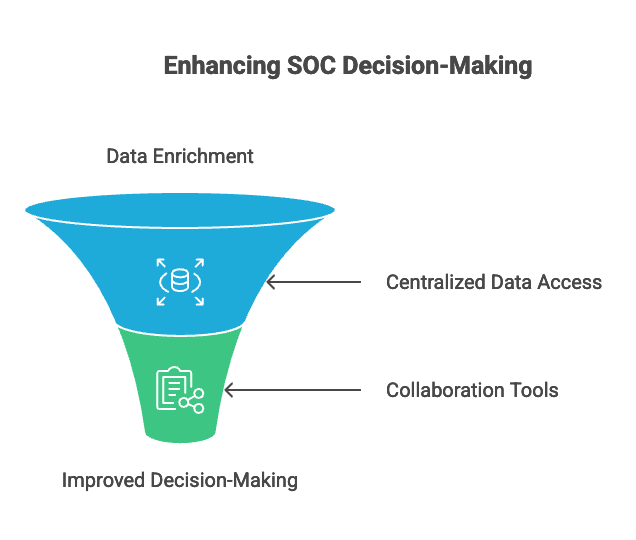
4. Empower Analysts with Context
Analysts need access to the right information at the right time to make informed decisions. This can be achieved through:
Enriched Alerts: Enrich alerts with contextual information such as asset details, user information, and threat intelligence data.
Centralized Data: Provide analysts with access to a centralized data repository that contains all relevant security information.
Collaboration Tools: Implement collaboration tools that allow analysts to easily share information and collaborate on investigations.
By empowering analysts with context, SOCs can improve their decision-making capabilities and reduce the time it takes to investigate security incidents.
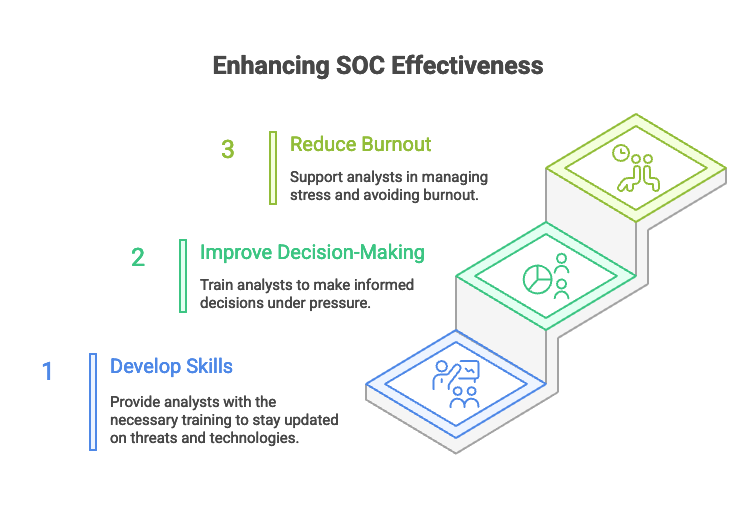
5. Invest in Training and Development
Finally, it's important to invest in training and development for SOC analysts. This will help them:
Develop their skills: Provide analysts with the training they need to stay up-to-date on the latest threats and security technologies.
Improve their decision-making: Train analysts on how to make informed decisions under pressure.
Reduce burnout: Provide analysts with the support they need to manage stress and avoid burnout.
By investing in training and development, SOCs can improve the overall effectiveness of their security operations.
The key to improving SOC effectiveness is not necessarily generating more alerts, but rather focusing on reducing the number of decisions analysts need to make. By improving alert fidelity, automating responses, prioritizing high-risk events, empowering analysts with context, and investing in training and development, SOCs can significantly reduce the workload on analysts, improve their response time to security incidents, and ultimately strengthen the organization's security posture. The shift from alert overload to decision support is crucial for building a resilient and effective security operations center.